OSI model
The Open Systems Interconnection Reference Model (OSI Model or OSI Reference Model for short) is a layered abstract description for communications and computer network protocol design, developed as part of the Open Systems Interconnect initiative. It is also called the OSI seven layers model.
Purpose
The OSI model divides the functions of a protocol into a series of layers. Each layer has the property that it only uses the functions of the layer below, and only exports functionality to the layer above. A system that implements protocol behavior consisting of a series of these layers is known as a 'protocol stack' or 'stack'. Protocol stacks can be implemented either in hardware or software, or a mixture of both. Typically, only the lower layers are implemented in hardware, with the higher layers being implemented in software.
This OSI model is roughly adhered to in the computing and networking industry. Its main feature is in the interface between layers which dictates the specifications on how one layer interacts with another. This means that a layer written by one manufacturer can operate with a layer from another (assuming that the specification is interpreted correctly.) These specifications are typically known as Request for Comments or "RFC"s in the TCP/IP community. They are ISO standards in the OSI community.
Usually, the implementation of a protocol is layered in a similar way to the protocol design, with the possible exception of a 'fast path' where the most common transaction allowed by the system may be implemented as a single component encompassing aspects of several layers.
This logical separation of layers makes reasoning about the behavior of protocol stacks much easier, allowing the design of elaborate but highly reliable protocol stacks. Each layer performs services for the next higher layer, and makes requests of the next lower layer. As previously stated, an implementation of several OSI layers is often referred to as a stack (as in TCP/IP stack).
The OSI reference model is a hierarchical structure of seven layers that defines the requirements for communications between two computers. The model was defined by the International Organization for Standardization in the ISO standard 7498-1. It was conceived to allow interoperability across the various platforms offered by vendors. The model allows all network elements to operate together, regardless of who built them. By the late 1970's, ISO was recommending the implementation of the OSI model as a networking standard.
Of course, by that time, TCP/IP had been in use for years. TCP/IP was fundamental to ARPANET and the other networks that evolved into the Internet. (For significant differences between TCP/IP and ARPANET, see RFC 871).
Only a subset of the whole OSI model is used today. It is widely believed that much of the specification is too complicated and its full functionality has taken too long to implement, although there are many people that strongly support the OSI model.
On the other hand, many feel that the best thing about the whole ISO networking effort is that it failed before it could do too much damage.
Description of layers
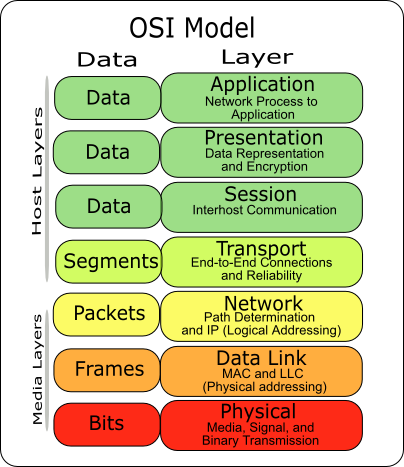
Layer 1: Physical layer
The physical layer defines all the electrical and physical specifications for devices. This includes the layout of pins, voltages, and cable specifications. Hubs and repeaters are physical-layer devices. The major functions and services performed by the physical layer are:
- establishment and termination of a connection to a communications medium.
- participation in the process whereby the communication resources are effectively shared among multiple users. For example, contention resolution and flow control.
- modulation, or conversion between the representation of digital data in user equipment and the corresponding signals transmitted over a communications channel. These are signals operating over the physical cabling -- copper and fibre optic, for example. SCSI operates at this level.
Layer 2: Data link layer
The data link layer provides the functional and procedural means to transfer data between network entities and to detect and possibly correct errors that may occur in the Physical layer. The addressing scheme is physical which means that the addresses (MAC address) are hard-coded into the network cards at the time of manufacture. The addressing scheme is flat. Note: The best known example of this is Ethernet. Other examples of data link protocols are HDLC and ADCCP for point-to-point or packet-switched networks and Aloha for local area networks. On IEEE 802 local area networks, and some non-IEEE 802 networks such as FDDI, this layer may be split into a Media Access Control (MAC) layer and the IEEE 802.2 Logical Link Control (LLC) layer.
This is the layer at which bridges and switches operate. Connectivity is provided only among locally attached network nodes.
Layer 3: Network layer
The data link layer is layer two of the seven-layer OSI model. It responds to service requests from the network layer and issues service requests to the physical layer.
The data link layer is the layer of the model which transfers data between adjacent network nodes in a wide area network or between nodes on the same local area network segment. The data link layer provides the functional and procedural means to transfer data between network entities and might provide provide the means to detect and possibly correct errors that may occur in the Physical layer. Examples of data link protocols are Ethernet for local area networks and PPP, HDLC and ADCCP for point-to-point connections.
The data link is all about getting information from one place to a selection of other places. At this layer one does not need to be able to go everywhere, just able to go somewhere else. So in social contact, one needs to know at least one other person, but not necessarily know Tung of Waterloo, Canada.
The data link provides data transfer across the physical link. That transfer might or might not be reliable; many data link protocols do not have acknowledgments of successful frame reception and acceptance, and some data link protocols might not even have any form of checksum to check for transmission errors. In those cases, higher-level protocols must provide flow control, error checking, and acknowledgments and retransmission.
This layer is sometimes split into two sublayers. The first sublayer is Logical Link Control (LLC). This sublayer multiplexes protocols running atop the data link layer, and optionally provides flow control, acknowledgment, and error recovery.
The second sublayer is Media Access Control (MAC). This sublayer determines who is allowed to access the media at any one time. There are generally two forms of media access control: distributed and centralised. Both of these may be compared to communication between people:
In a network made up of people speaking, i.e. a conversation, we look for clues from our fellow talkers to see if any of them appear to be about to speak. If two people speak at the same time, they will back off and begin a long and elaborate game of saying "no, you first". In the UK Houses of Parliament, the speaker determines who can speak at any time and gets to say "order" very loudly if anybody breaks the rules. The Media Access Control sublayer also determines where one frame of data ends and the next one starts. In a snail-mail network, each letter is one frame of data, and you can tell where it begins and ends because it is inside an envelope. You might also specify that a letter will begin with a phrase like "Dear Sir", and ends with a phrase like "Yours Sincerely".
On IEEE 802 local area networks, the data link layer is split into MAC and LLC sublayers; this means that the IEEE 802.2 LLC protocol can be used with all of the IEEE 802 MAC layers, such as Ethernet, Token Ring, IEEE 802.11, etc., as well as with some non-802 MAC layers such as FDDI. Other data link layer protocols, such as HDLC, are specified to include both sublayers, although some other protocols, such as Cisco HDLC, use HDLC's low-level framing as a MAC layer in combination with a different LLC layer.
Layer 4: Transport layer
The transport layer provides transparent transfer of data between end users, thus relieving the upper layers from any concern with providing reliable and cost-effective data transfer. The transport layer controls the reliability of a given link. Some protocols are stateful and connection oriented. This means that the transport layer can keep track of the packets and retransmit those that fail. The best known example of a layer 4 protocol is TCP.
Layer 5: Session layer
The session layer provides the mechanism for managing the dialogue between end-user application processes (By dialog we mean that whose turn it is to transmit). It provides for either duplex or half-duplex operation and establishes checkpointing, adjournment, termination, and restart procedures (keeping a track so as to restart from the very same point where they had left in case of a crash). This layer is responsible for setting up and tearing down TCP/IP sessions.
Layer 6: Presentation layer
The presentation layer relieves the Application layer of concern regarding syntactical differences in data representation within the end-user systems. MIME encoding, data compression, encryption, and similar manipulation of the presentation of data is done at this layer. An example of a presentation service would be the conversion of an EBCDIC-coded text file to an ASCII-coded file or serializing objects and other data structures into and out of XML.
Layer 7: Application layer
The application layer interfaces directly to and performs common application services for the application processes. The common application services provide semantic conversion between associated application processes. Examples of common application services include the virtual file, virtual terminal (for example, Telnet), transfer and Manipulation protocol" (JTM, standard ISO/IEC 8832).
Interfaces
In addition to standards for individual protocols in transmission, there are also interface standards for different layers to talk to the ones above or below (usually operating-system-specific). For example, Microsoft Windows's Winsock and Unix's Berkeley sockets and System V Streams are interfaces between applications (layers 5 and above) and the transport (layer 4). NDIS and ODI are interfaces between the media (layer 2) and the network protocol (layer 3).
Table of examples
| Layer | Misc. examples | TCP/IP suite | SS7 | AppleTalk suite | OSI suite | IPX suite | SNA | UMTS |
|---|---|---|---|---|---|---|---|---|
| 7 - Application | HL7, Modbus, SIP | HTTP, SMTP,SMPP SNMP, FTP, Telnet, NFS, NTP | ISUP, INAP, MAP, TUP, TCAP | AFP, PAP | FTAM, X.400, X.500, DAP | APPC | ||
| 6 - Presentation | TDI, ASCII, EBCDIC, MIDI, MPEG | XDR, SSL, TLS | AFP, PAP | |||||
| 5 - Session | Named Pipes, NetBIOS, SAP, SDP | Session establishment for TCP | ASP, ADSP, ZIP | NWLink | DLC? | |||
| 4 - Transport | NetBEUI | TCP, UDP, RTP, SCTP | ATP, NBP, AEP, RTMP | TP0, TP1, TP2, TP3, TP4, OSPF | SPX, RIP | |||
| 3 - Network | NetBEUI, Q.931 | IP, ICMP, IPsec, ARP, RIP, BGP | MTP-3, SCCP | DDP | X.25 (PLP), CLNP | IPX | RRC (Radio Resource Control) | |
| 2 - Data Link | Ethernet, Token Ring, FDDI, PPP, HDLC, Q.921, Frame Relay, ATM, Fibre Channel | MTP-2 | LocalTalk, TokenTalk, EtherTalk, Apple Remote Access, PPP | X.25 (LAPB), Token Bus | IEEE 802.3 framing, Ethernet II framing | SDLC | MAC (Media Access Control) | |
| 1 - Physical | RS-232, V.35, V.34, Q.911, T1, E1, 10BASE-T, 100BASE-TX, ISDN, SONET, DSL | MTP-1 | Localtalk on shielded, Localtalk on unshielded (PhoneNet) | X.25 (X.21bis, EIA/TIA-232, EIA/TIA-449, EIA-530, G.703) | Twinax | PHY (Physical Layer) |
Parallel

Humor
The 7 layer model has often been extended in a humorous manner, to refer to non-technical issues or problems. A common joke is the 9 layer model, with layers 8 and 9 being the "financial" and "political" layers.
Network technicians will sometimes refer euphemistically to "layer-eight problems," meaning problems with an end user and not with the network.
The OSI model has also on occasion been jokingly called the "Taco Bell model", since the restaurant chain has been known for their 7 layer burrito.
Dick Lewis uses an analogy of James Bond delivering classified messages to illustrate the seven-layer model.
